Who might be harmed and how. Describe the funding mechanism contract inter-agency agreement that the.
Security Risk Assessment Template Excel
Click to View PDF.
Privacy risk assessment template. Nonprofit Board Meeting Agenda Template – 32238 views. Deciding what steps youll need to work through The scale and complexity of your PIA will depend on the scale and complexity of your project. Blank Notarized Letter for Proof of Residency Template PDF Format – 11745 views.
A Threat Risk Assessment TRA is a process for assessing documenting and addressing risk to information assets. The MVROS was identified as a potential high-risk system in the Departments annual enterprise risk assessment. Privacy impact assessments PIAs for electronic information systems and collections1.
Check-in procedures patient identity verification insurance etc. This focus area includes but is not limited to risk models risk assessment methodologies and approaches to determining privacy. What is a PIA used for.
A privacy impact assessment PIA is one of the most important instruments through which the. A final easily overlooked step when conducting a privacy risk assessment in clinical areas is to ensure PHI shred bins are being emptied regularly. Lewis recently discussed with the Journal some tips for devising a framework for a risk assessment and to provide a reminder about why theyre needed.
The risk assessment will be utilized to identify risk mitigation plans related to MVROS. Identify and mitigate data breach risks. A security risk assessment has been conducted.
Only go as far as you. Monitoring testing or evaluation has been undertaken to safeguard the information and prevent its misuse. What youre already doing to control the risks.
Rather provide a holistic view of the risks to privacy. By conducting privacy threshold analyses PTAs and PIAs in accordance with the policies and. Provides guidance on how you can screen for potentially high privacy risk projects by completing a threshold assessment to determine whether a PIA is required.
When the action is needed by. 6 Three Stages of a PIA Stage 1 – The initial screening questions This section is to be completed by the service manager or project lead responsible for delivering the proposed change. A privacy risk assessment is not required by HIPAA.
Includes a template to assist you complete a threshold assessment. One approach to guarantee that all dangers are assessed similarly is to utilize a risk assessment form. WinRar DOC PDF XLSX To use this PDF file you need Adobe.
Agencies obligations with respect to managing privacy risk and information resources extends beyond compliance with privacy laws regulations and policies. You can use a risk assessment template to help you keep a simple record of. The assessment is a practical method of evaluating privacy in information systems and collections and documented assurance that privacy issues have been identified and adequately addressed.
Risks ought to be deliberately recognized and explored to guarantee those things exercises circumstances forms and so forth that reason damage to individuals or property are controlled. Template for Data Protection Impact Assessment DPIA This template published by Family Links Network provides a list of questions related to data protection issues that should be considered by National Societies prior to conducting a DPIA. Appropriate security controls have been identified and implemented to protect against risks identified in security risk assessment.
Risk and Audit departments are experts in risk management and are often informed by standards such as ISO31000. A risk management template to record any risks you identify and what you can do to mitigate them. Scope of this risk assessment The MVROS system comprises several components.
It is likely that much processing activity is being conducted by external data processors on behalf of your organization. Privacy and mitigate the risks described in the previous bullet. Additionally consider the following as appropriate to the project.
Do not list every privacy risk in the succeeding analysis sections. Rather a privacy risk assessment is a best practice to ensure that an organization isnt at risk for a breach. Privacy and Data Protection Risk Assessment Questionnaire Notice.
Compliance Counseling Risk Assessment Training Breach Response Workshops Breach Coaching Litigation Class Action Regulatory Defense We live data privacy 247. Employee Work Schedule Template Excel – 13964 views. The template is split up into the following sections.
Thank You Letters To Veterans Example – 11414. A privacy impact assessment checklist or privacy impact assessment examples will often include the need to identify your purpose for the PIA assessment. Response Yes No Some Has your business area provided notice to each.
Sets out the benefits of conducting a PIA even when a project does not meet the high privacy risk threshold and. Conference Plan Template – 17466 views. These standards can advise on building risk registers assessing mitigating and monitoring risk.
Download Sample Letter of Intent to Renew Employment Contract – 26430 views. Risk Assessment Form Template 40 Examples. What further action you need to take to control the risks.
Owners on the mitigation of potential privacy risks. PIA Template asks a number of questions aimed at addressing these requirements. Here are several of the reasons for using a data privacy risk assessment template to generate a PIA data protection report.
Threats and risks are articulated in relation to how sensitive or valuable the information is and what vulnerabilities are inherent in the environments through which the information passes is stored or is used. A process that helps organizations to analyze and assess privacy risks for individuals arising from the processing of their data. Who needs to carry out the action.
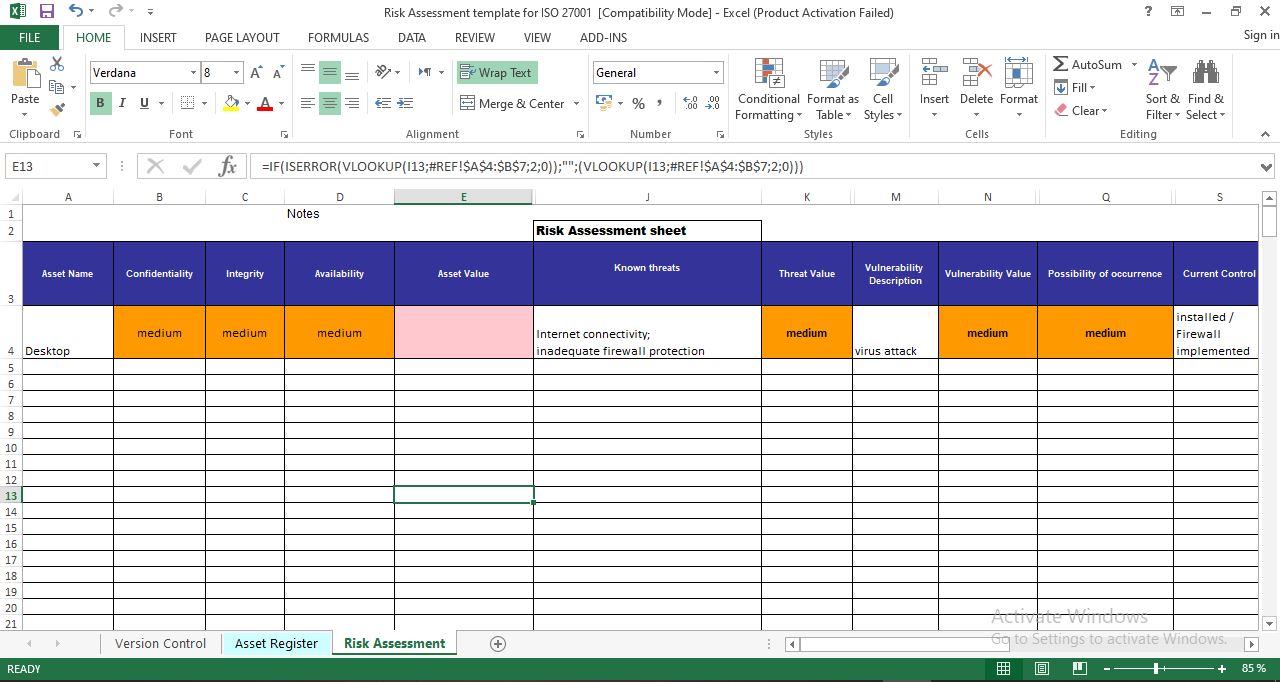
Risk Assessment Template For Iso 27001
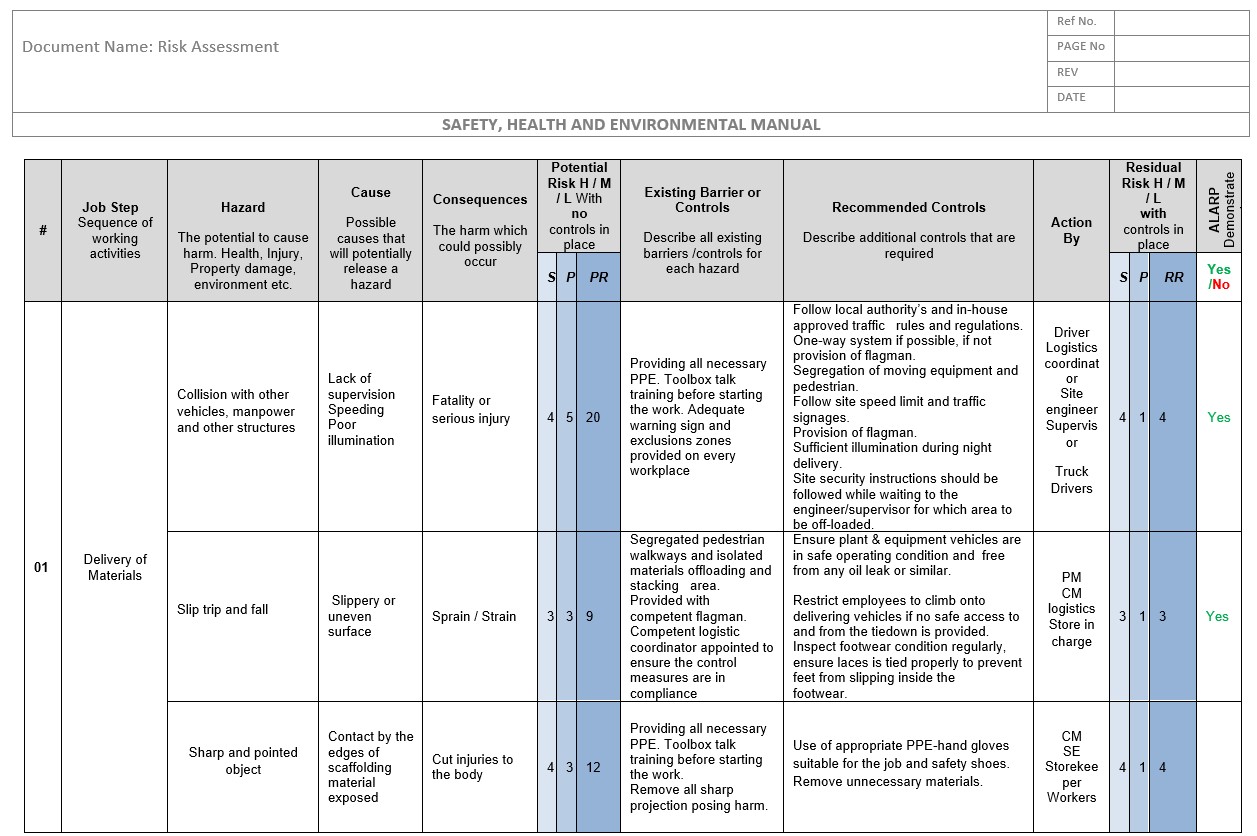
Risk Assessment Template For Column Wall Other Vertical Elements Cast In Situ
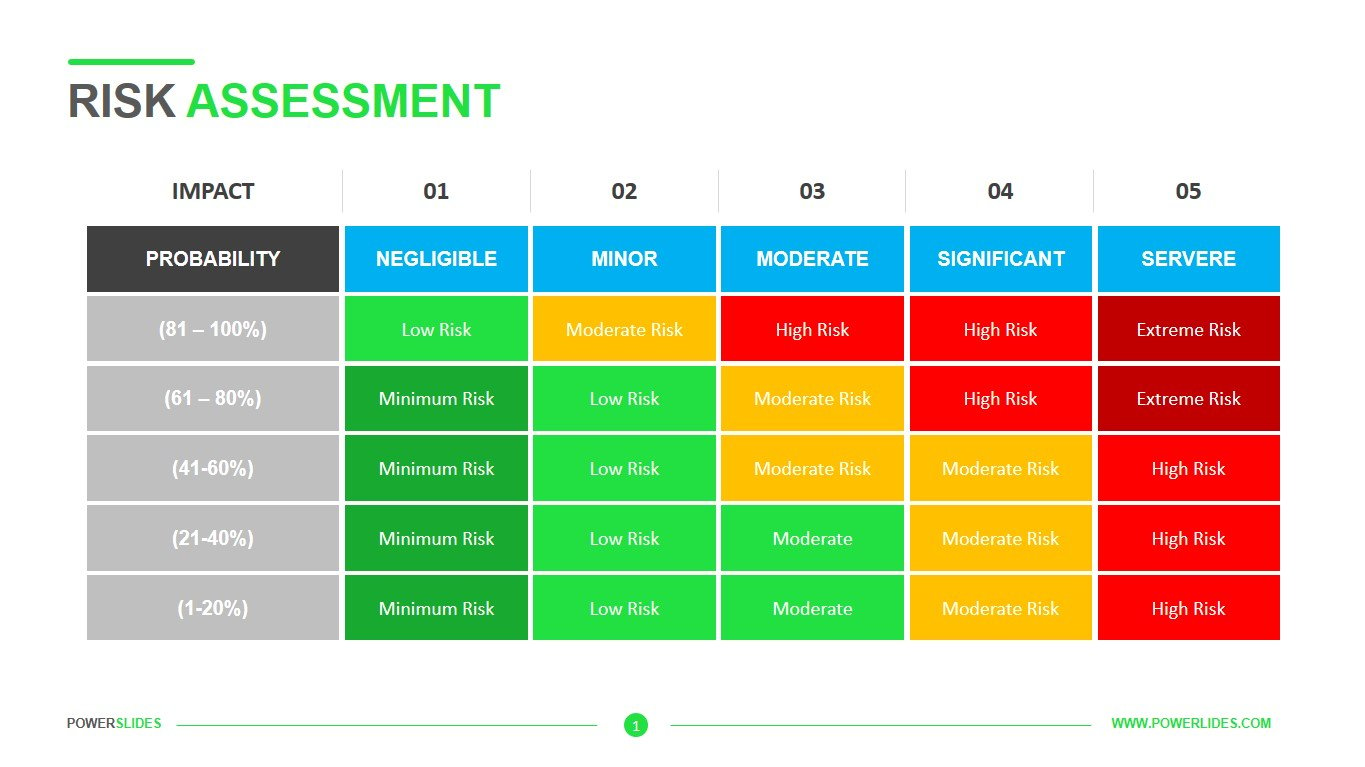
Risk Assessment Template Download Now Powerslides
Compliance Risk Assessment Template Excel