Monitor the traffic coming in and going out your firewall and read the reports carefully. Servers routers workstations gateways must all be checked to make sure they are secure and safe and arent sharing any sensitive information.

Physical Security Checklist Template Beautiful Physical Security Checklist Continued E4930r0003 Checklist Template Inspection Checklist Checklist
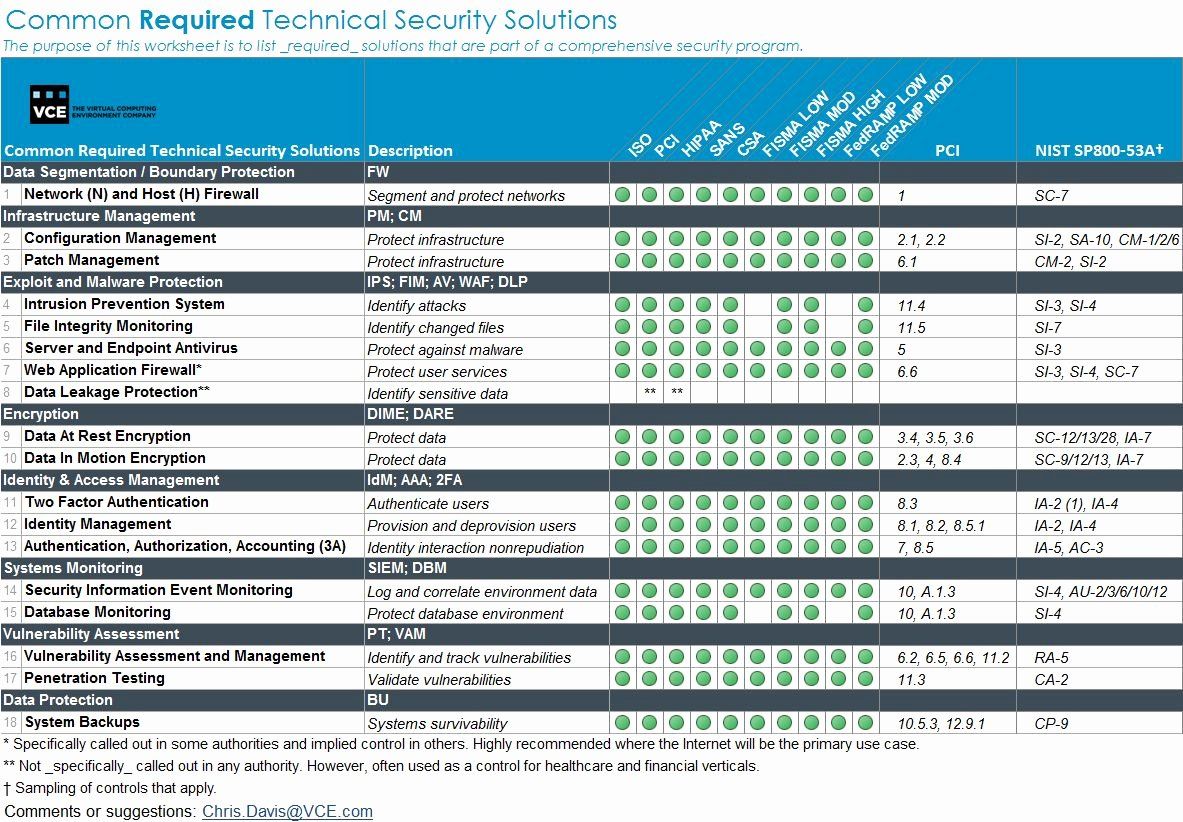
It managers and network security teams can use this digitized checklist to help uncover threats by checking the following itemsfirewall computers and network devices user accounts malware software and other network security protocols.
Network security checklist pdf. Are you using a strong encryption on your wireless networks. Security Audit Checklist Template. 4 Review the procedure management system.
The network device is secured in an area with physical access control. Types of Security Solutions. 40 YN _____ If.
This template comes with a file containing an example of a security audit checklist that can assist you as a guide to making one for your needs. NOTES 5 51. If machine is a new install protect it from hostile network traffic until the operating system is installed and hardened.
Network security management Communications security. 7 Check the penetration testing process and policy. Now that you understand the basics of network security review these six steps to create a holistic security solution for your small business.
Consider the harm a network security breach could do to your business such as lost revenue or customer litigation. 1412 Securing application services on public networks Defined policy for securing application services on public networks. This checklist is designed to assist in a quick review of your organizations network security planning.
Network Security Checklist By Alex Strickland General Develop a Security Policy detailing rights and responsibilities of staff patrons and contract users Develop a Acceptable Use Policy AUP developed for patrons and staff Train staff not to reveal system passwords to anyone other than speci-fied individuals. Education Network Security Checklist. The wireless device supports ISO-approved encryption methods.
Network security at its heart focuses on interactions interactions between computers tablets and any other devices a company uses. This checklist is not meant to be exhaustive or exclusive as there are pre-NSL rules and regulations as well as NSL. 6 steps to secure your network.
This checklist of the Network Security Law of China NSL summarizes the key requirements and highlights the most important actions required by the NSL that took effect on 1 June 2017. This template is available to be downloaded in PDF format. Network Checklist final a 3 of 3 revised 51809 Wireless Security 37.
Only use Supported Windows Operating systems and applications. 3 Make sure all procedures are well documented. 514 YN _____ If No skip to item 40.
This checklist does not provide vendor specific security considerations but rather attempts to provide a generic listing of security considerations to be used when auditing a. The wireless device adheres to minimum levels of security developed by the ISO. Read on to access our network security best practices checklist.
Network and Security Checklist. Is the network device considered a Core network device as defined by the standard. Network Security Internal Audit Checklist.
This document focuses on three key areas. Networking Do you have a hardware irewall and is it under support by the manufacturer. ISO 27001 CHECKLIST TEMPLATE ISO 27001 CONTROL IMPLEMENTATION PHASES TASKS IN COMPLIANCE.
What Is Network Security. 2 Record the audit details. Microsoft no longer supports XP and Windows 2003 server.
Data and Network Security Checklist About IronEdge. Risk management Cybersecurity Data privacy INSTRUCTIONS Use the checklist as a tool to research and collect information on. The following tips can help you develop and win support for an effective network security plan.
Point Network Security Checklist. Ultimate Network Security Checklist. The core network device is attached to an.
Is the irewall coniguration clean and operating system up to date. 5 Assess training logs and processes. No skip to item.
Re-secure network with new passwords and training of employees on security best practices Average Cost of Service Between actual equipment costs and the fees for service network maintenance and repairs range from as little as 100 or less to upwards of 10000. The core network device is located in an alarmed area. Improving and maximizing network security helps prevent against unauthorized intrusions.
5Router and the wiring. PDF Template A network security audit checklist is used to proactively assess the security and integrity of organizational networks. Do you have a monitored Intrusion Detection System in place.
Dont rely on alerts to flag dangerous activity. A Network Security Audit is an audit of all your network systems to make sure that potential security risks are eliminated or minimized. UCD IT Services IT Security Windows Server Security Checklist System Installation Patching 1.
6 Review security patches for software used on the network. Is your online information secured. Is this network device a wireless network device.
Steps on How to Secure Your Network. Focus on return on value rather than return on investment. Firewall network appliance Craig Simmons October 2000 Introduction This checklist should be used to audit a firewall.
Never assume that network attacks will come only from outsiders. 1 Introduction to Network Security Audit Checklist. FREE 5 Network Security Checklist Templates in PDF.
Checklist for Network Security. Closely monitor your traffic.

Physical Security Inspection Checklist Lovely 28 Of Blank Security Checklist Template Security Audit Security Report Report Template

Pin On Assessment

Security Audit Checklist Template Security Audit Checklist Template Checklist
It Infrastructure Assessment Template Inspirational 28 Of Security Audit Checklist Template Security Audit Checklist Template Security Assessment